Mobile acquired data technologies have come a long way and are now suitable for almost all settings. However, the MAD Research series showed the concerns of many individuals and groups considering taking the leap and ‘going digital’ share some common themes.

- MAD performance in scenarios with low (or no) internet connectivity
- How to manage appropriate use of mobile devices among fieldworkers
- Capturing consent and multimedia
- Data security
Low (or no) internet connectivity
Thankfully, you do not need an internet connection to collect mobile data. One of the key advantages of CommCare as a Mobile Acquired Data platform is that it can be used to register and link case data offline in remote areas. This means data can be saved to the device and used to inform subsequent data collection without syncing to the internet. Data should still be synced to the server at the end of each day. Always consult with in country partners about which providers are used in the study area. Using dual-sim devices can help provide a second available data connection when real-time data connectivity is important. Other options for low connectivity areas include using mobile broadband devices (e.g. dongles with micro usb converters) for syncing data in the evenings.
Mobile devices
Selecting and purchasing mobile devices
Selecting the right mobile devices for the particular setting of a project can be difficult the first time using MAD technology.

Basic capabilities
Most smart devices (i.e. smartphones and tablets) are capable of running CommCare and other MAD platforms. However, CommCare is only available on Android software which makes any Apple device a no-go.
Size matters
The next consideration is whether to select a tablet or smartphone as the device for your frontline workers. The main practical difference here is the size of the screen. Tablets allow more questions to be displayed on a single screen (5-7 as opposed to 3-5 on a smartphone). This helps for referring to multiple questions. Another benefit of tablets is that it is easier to view images on them, (though they don’t always come with great cameras). Smartphones have the advantage of being easier to hold in one hand. This is particularly useful when taking physical measurements during fieldwork. Enumerators are sometimes also more accustomed and comfortable using smartphones.
Purchasing devices
Devices are generally more cost effective in-country, and repairs and replacement parts are more readily available. Purchasing in-country is also less challenging for projects as no importation of devices (and payment of associated taxes) is required. Device cases are important and should be budgeted for. It is also recommended to buy a few extra devices as spares - you never know if you’ll need them, but you’ll be glad to have them if you do!
Managing mobile devices
"If, for example, one network is down, then we have a spare sim card to upload the data in the cloud. Also, we made sure that we have the Powerbank just in case" - Christian Genoa, App Builder, Vietnam Vegetables project
Once you have your devices, you’ll need to know the top tips for managing them during fieldwork!
Battery life
Make sure your field implementation plan includes charging mobile device batteries every night. Keep spare battery packs (and powerbanks) with each supervisor / team leader. Keep device batteries above 10% to ensure they don’t run out of power during the middle of an activity. More battery tips for low electricity settings are available here.
Data
Managers need to be proactive in ensuring that enumerators do not use up available mobile data (i.e. internet) for personal uses during fieldwork. Be sure to remind enumerators that the project devices are for work use and are not to be used as personal devices particularly in relation to data use. Be sure to remind them that app usage information for each device can be checked by supervisors / team leaders. As a precaution, supervisors should always have spare data packages available to top up enumerators who run out during fieldwork.
Capturing consent and multimedia
One benefit from adopting MAD is that it allows frontline workers to capture data beyond text. Photos and video can be captured and tagged with additional metadata (e.g. date and time, GPS location). This gives frontline workers a structure for capturing interesting and unexpected stories they encounter during fieldwork. However, it is crucial that project and program managers build in consent forms into these activities. MAD apps can capture consent as free hand drawing (for signing) and as voice recordings for non-literate respondents. As MAD technology makes photography easier to integrate into other data collection activities, managers should aim to provide guidance to frontline workers in capturing better photos. Basic instruction in subject, visual composition, lighting, and writing appropriate photo captions can greatly improve the quality of images produced in the field. The MAD Research Series produced some excellent training materials in basic photography. These are summarised in the subsections below. You can review further information and more tips on multimedia data capture in this MAD Masterclass ‘Story Capture’ presentation.
Subject
When you are taking a photo, you should know what your subject is - what are you taking a photo of? Be clear about this, and make sure it is in focus. To make sure they are in focus, touch them on the screen and make sure the screen locks focus on them. In photographs with multiple subjects or objects, the key subject will be the one that is usually in focus or in a key part of the photo.
Visual composition
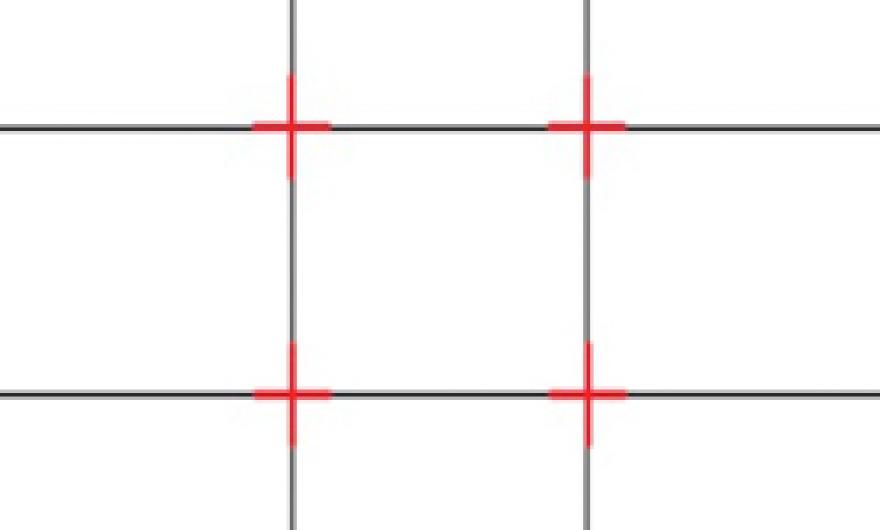
The act of positioning a person/object in the photo is known as composition. How you position the main person or object in your photo is crucial. The best way to describe this is through the rule of thirds. This is applied by aligning a subject with the guidelines and their intersection points, placing the horizon on the top or bottom line, or allowing linear features in the image to flow from section to section. Use the gridlines on your phone camera (see camera settings) to align horizons to the lines or put subjects in the cross points. See example below:
Lighting
Outdoor lighting is worst in the middle of the day (too bright). If you are taking outdoor photos at this time of day use shaded areas to photograph in indirect light (i.e. not in the sun). Many professional photographers aim to shoot during the sunrise and sunset hours because the light at this time of day is especially good. For indoor photos, try to use natural light coming from a window or doorway on your subject. Avoid photographing something directly underneath an overhead light (get them to take a step back).
Camera angle
The main four options (see examples below) are:
- Eye to eye (photo taken same level as subject, indicates equality)
- Bird’s eye view (Photo taken from above, position of power)
- Point of view (photo taken from first-person perspective, places viewer in scene)
- Child’s perspective (Photo taken from low angle looking up at subject, subject in position of power
When submitting a photo as part of your research it is important to also provide an accompanying caption. These few sentences of information are crucial in ensuring the image has context and can be used accurately. A caption should include succinct information that answer the following:
- Who is in the photo?
- Where is the photo taken?
- What is happening in the photo?
- Why is this important for the project?

Amber from Oikoi assists a NARI staff member during a CommCare training delivered by AgImpact at the NARI research station in Leh, in Eastern Highlands Province of Papua New Guinea. AgImpact is delivering a Short Research Assignment for ACIAR exploring the uptake of using apps on tablets for agricultural research. CommCare is the software that was chosen through an earlier pilot test, it was deemed the most flexible and adaptive for the working environments where ACIAR funds research for agricultural development projects.
Data security
The last MAD topic that kept coming up during the research series was around data security. CommCare’s data security system is world class, and is trusted by donors (USAID), UN bodies (World Health Organization, World Food Programme, UNICEF), universities (Harvard University) and NGOs (CARE International). Within digital data collection, areas of digital data vulnerability include: i) on the mobile device, ii) in transit, iii) on the server, and iv) when stored locally for analysis. How data is protected in each of these areas is outlined below.
On the device
Data collected via CommCare and stored on the mobile device are encrypted (256 bit), and can only be decrypted with the correct username and password. Usernames and passwords are unique to each user in a CommCare app and can be controlled by a central app manager (via the CommCare HQ webpage). Central managers can also set whether data that has been collected is available for review by frontline workers and data cannot be altered by frontline workers once it has been entered and saved. Login timeouts can also be pre-set in CommCare to avoid data vulnerability on the devices.
In transit to the cloud
Data in transit from devices to the secure server, or from the secure server to your computer uses 256 bit encryption and is transported by Secure Sockets Layer (SSL). A 256 bit encryption meets the AES (Advanced Encryption Standard). How secure is it? Well breaking a symmetric 256-bit key by brute force requires 2128 times more computational power than a 128-bit key. This means fifty supercomputers that could check a billion billion (1018) AES keys per second (if such a device could ever be made) would, in theory, require about 3×1051 years to exhaust the 256-bit key space.
On the cloud server
Data is hosted by Dimagi (creators of CommCare) in a HIPAA compliant, enterprise-grade ISO 27001 compliant data centre in the United States. Data on the server is secured with at-rest encryption and is backed up offsite daily. Access to the data centre is controlled with biometric security, it is a climate controlled facility and has intrusion monitoring. Access to your data is controlled by you through CommCareHQ web portal. Any changes to security policy are transparent and you will be notified of any changes.
Locally stored on your computer
Once data is downloaded from the secure server on to your local computer for analysis, they become your responsibility to manage securely. Importantly, local storage of data on individual computers is the least secure point in the security chain. Staff should always use password protected spreadsheet files for local security. Data exports from the CommCare server can be set up as de-identified to remove personal details of respondents. The export feature also allows for particular columns to be marked as containing sensitive data. If data are lost or corrupted on a local computer, they can be re-exported from the cloud server. Find more tips on data security in the MAD Showcase ‘Key App Data Issues’ presentation here.